Understanding DDoS Attacks: How They Work and How to Defend Against Them
A Distributed Denial of Service (DDoS attack is a type of cyber attack in which multiple compromised systems flood a targeted server, service, or network, overwhelming it with traffic. This makes the targeted service unavailable to legitimate users. DDoS attacks are a significant threat to online businesses, government sites, and any organization reliant on internet accessibility. In this post, we’ll explore how DDoS attacks work, the different types, and critical steps for protection.
What is a DDoS Attack?
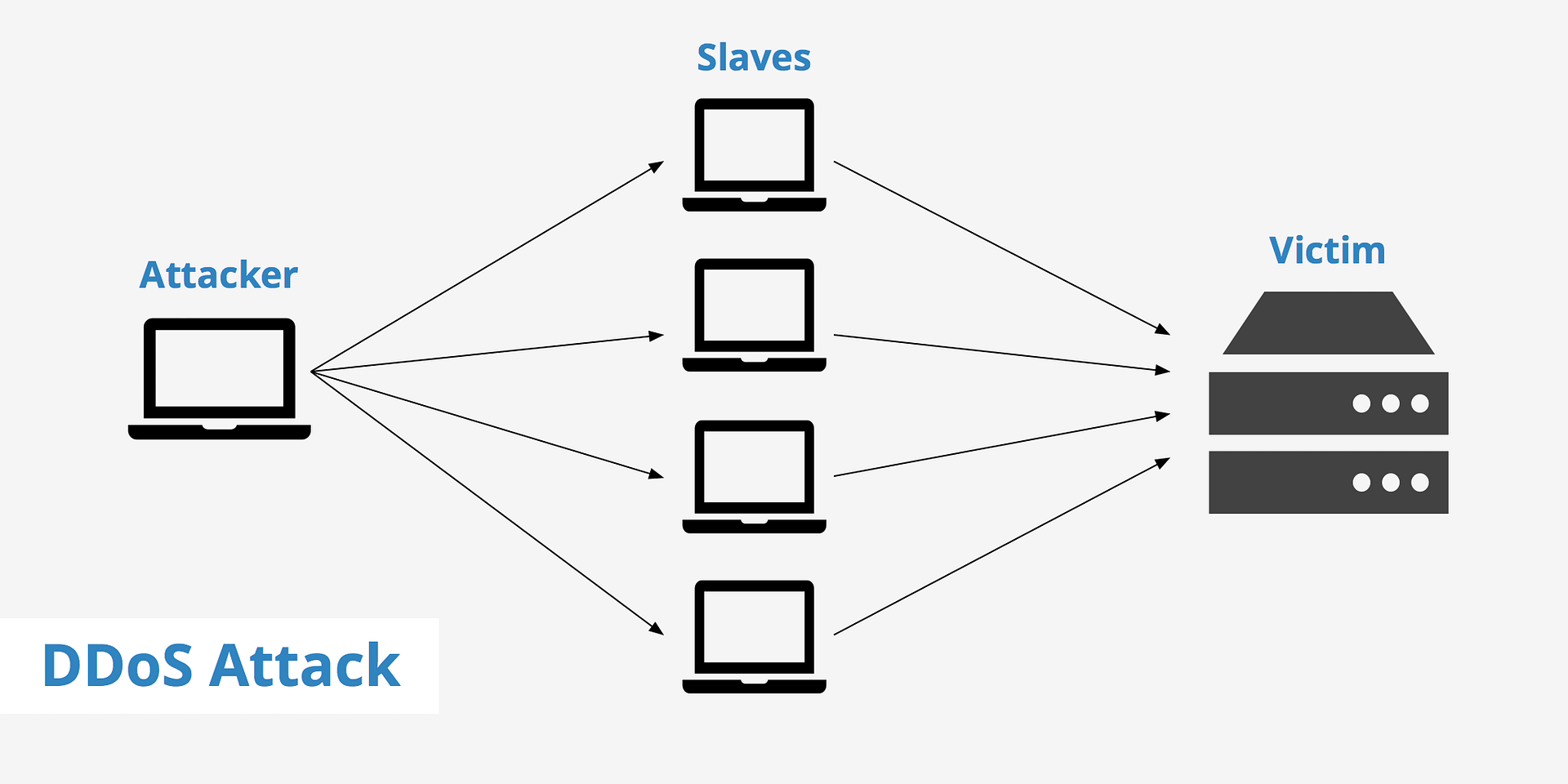
In a DDoS attack, an attacker uses multiple systems, often compromised devices known as a botnet, to send a massive number of requests to a single target. The goal is to exhaust the target’s resources, such as bandwidth, processing power, or memory, rendering it unable to serve legitimate requests. This results in a temporary or prolonged denial of service for users attempting to access the targeted site or service.
For example, an e-commerce website under a DDoS attack may become sluggish or entirely inaccessible, leading to lost sales, customer frustration, and potential reputational damage.
How Does a DDoS Attack Work?
The typical DDoS attack involves the following steps:
- Infection and Compromise: The attacker first creates or rents a botnet, which is a network of infected devices. These devices may include computers, IoT devices, routers, and even smartphones. Users often remain unaware that their devices are compromised.
- Attack Command: The attacker issues a command to the botnet, instructing all compromised devices to send requests to the target server or network. Since each bot represents a different IP address, it becomes challenging for the target to block incoming traffic effectively.
- Overload and Service Disruption: The botnet floods the target with traffic, exhausting its resources and causing it to slow down, crash, or become entirely unresponsive. The target may be overwhelmed for hours or even days, depending on the attack’s scale and the defenses in place.
Types of DDoS Attacks
Understanding the different types of DDoS attacks can help organizations and individuals better recognize and defend against them. Here are the main categories:
- Volume-Based Attacks: These attacks focus on overwhelming the target with massive amounts of traffic. Methods include UDP floods (flooding the network with User Datagram Protocol packets) and ICMP floods (ping floods). The goal is to saturate the network bandwidth.
- Protocol Attacks: These attacks exploit weaknesses in the server or network protocol. Examples include SYN floods, where attackers send multiple SYN requests but never complete the handshake, leaving the server’s connection pool exhausted.
- Application Layer Attacks: Also known as Layer 7 attacks, these target specific applications rather than the whole network. An example is an HTTP flood, where attackers mimic legitimate user behavior to overwhelm the application server. Since these attacks look like regular traffic, they are harder to detect and mitigate.
For more in-depth resources on DDoS protection and cyber defense, check out computese.com.
Real-Life Examples of DDoS Attacks
DDoS attacks have affected some of the world’s largest websites and services. For example, in 2016, a major DDoS attack targeted Dyn, a DNS provider for sites like Twitter, Netflix, and Spotify, resulting in widespread outages. Another example is the Mirai botnet attack, which hijacked IoT devices, flooding services with massive amounts of traffic and affecting websites worldwide.
How to Protect Against DDoS Attacks
Although DDoS attacks can be challenging to prevent entirely, there are several effective strategies for reducing risk:
- Use a Content Delivery Network (CDN): CDNs distribute content across multiple servers worldwide. By using a CDN, you reduce the burden on your primary server and increase redundancy, which can help absorb the impact of a DDoS attack.
- Deploy Anti-DDoS Solutions: Many anti-DDoS services can detect and mitigate attacks before they reach your network. These include services offered by companies like Cloudflare and AWS Shield, which help filter malicious traffic and protect your site from large-scale attacks.
- Implement Rate Limiting: Rate limiting restricts the number of requests a user or IP address can make to your server within a certain period. This helps to minimize the effect of certain types of DDoS attacks, particularly HTTP floods and other Layer 7 attacks.
- Monitor Network Traffic: Regular network monitoring allows you to detect unusual traffic patterns and respond before the attack escalates. Many security platforms provide real-time monitoring and alerting features that help you quickly identify DDoS symptoms.
- Have a DDoS Response Plan: A well-prepared DDoS response plan can make a difference in minimizing downtime. Your plan should include steps for detecting attacks, informing relevant teams, contacting anti-DDoS services, and communicating with users and customers.
- Invest in Redundant Network Infrastructure: Using load balancing and geographically distributed servers can improve your network’s ability to withstand an attack. By spreading the load, you reduce the impact of incoming traffic on any single server, minimizing the potential for total downtime.
Staying Protected in an Increasingly DDoS-Prone World
With the rising number of DDoS attacks and increasing botnet capabilities, it’s essential to stay vigilant. Even though DDoS attacks can be difficult to fully prevent, being aware of the risk and using preventive measures can significantly reduce their impact. Implementing layered security measures like CDNs, rate limiting, and continuous monitoring can protect your online assets and keep your business running smoothly.
For further resources on network security and DDoS defense, explore our guides on computese.com.
Additional Resources
For more information on DDoS mitigation and cybersecurity, visit the trusted Cybersecurity & Infrastructure Security Agency (CISA) at cisa.gov or review insights on DDoS protection best practices from Krebs on Security.