Understanding Man-in-the-Middle (MITM) Attacks: How They Work and How to Protect Yourself
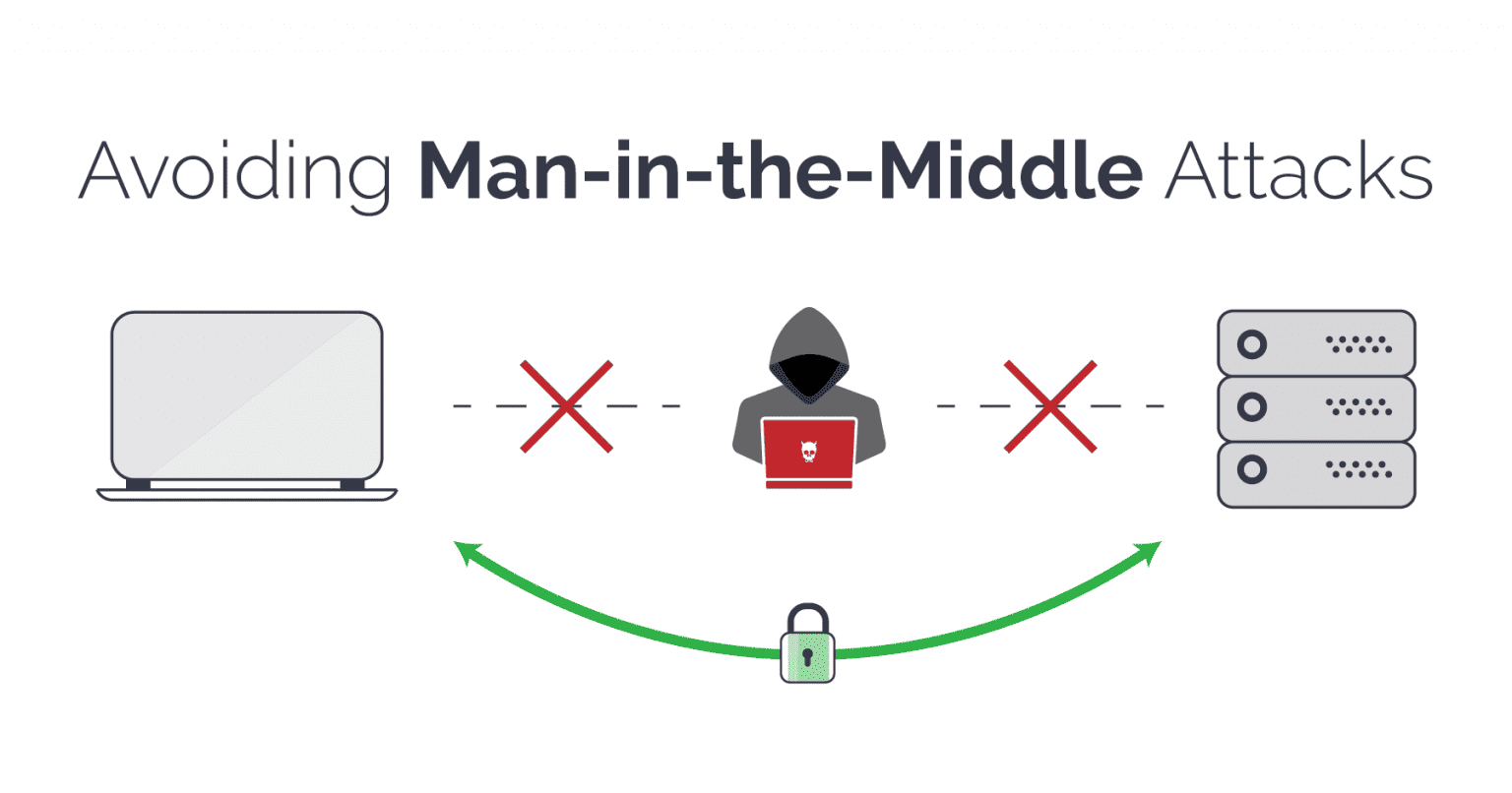
A Man-in-the-Middle (MITM) attack is a common yet severe cyber threat, where an attacker secretly intercepts communication between two parties, aiming to steal data, alter messages, or compromise security. This article will break down how MITM attacks work, provide real-life examples, and share essential tips to protect your data from these cyber threats.
What is a Man-in-the-Middle (MITM) Attack?
In simple terms, a MITM attack happens when an attacker positions themselves between two parties in a communication line, like two devices, making it appear that they are directly communicating with each other. However, the attacker can see, alter, and sometimes control the data exchange. Because the parties believe they are connected securely, they might share sensitive information, unaware that it is exposed.
A MITM attack can occur on various networks and devices, including public Wi-Fi, personal computers, mobile devices, and even corporate networks. Common targets include websites that handle personal information, financial transactions, and sensitive business data.
How Does a Man-in-the-Middle Attack Work?
Understanding how MITM attacks work can help us protect ourselves. Here’s a breakdown of how these attacks typically unfold:
- Interception: The attacker first finds a way to intercept the communication. This could happen through a variety of techniques, such as DNS spoofing (redirecting requests to malicious sites), ARP spoofing (altering local network routes), or even setting up a fake Wi-Fi network. Attackers often use public Wi-Fi networks as these are typically less secure and open to many users.
- Decryption and Eavesdropping: Once the attacker is in the middle, they decrypt the data, allowing them to eavesdrop on everything sent between the two parties. They can capture login credentials, credit card information, private messages, or any other unencrypted data.
- Modification: With access to the data, an attacker may also modify it. For instance, in an online banking session, they could alter payment details, effectively diverting money to their own account. They can even alter messages or documents being exchanged in real-time, causing severe consequences for the user.
Real-Life Examples of MITM Attacks
One high-profile MITM attack occurred in 2015 when Superfish, a pre-installed adware on Lenovo laptops, enabled attackers to intercept encrypted traffic. The program created a backdoor, making users vulnerable to attacks on secure websites. In another example, public Wi-Fi networks have often been exploited by hackers who create fake Wi-Fi connections that mimic legitimate ones, tricking users into connecting and thereby gaining access to sensitive data.
For more information on network vulnerabilities and to learn more about cybersecurity, explore our resources at computese.com.
Types of MITM Attacks
Understanding the different types of MITM attacks can help users recognize threats more easily:
- DNS Spoofing: Attackers alter DNS (Domain Name System) records, redirecting users to fake websites where they unknowingly input sensitive information.
- Wi-Fi Eavesdropping: Hackers create fake Wi-Fi networks that mimic legitimate ones, intercepting all information sent by users connected to them.
- Session Hijacking: Attackers gain access to a session token, enabling them to access a user’s account and impersonate them in real-time.
How to Protect Yourself Against MITM Attacks
While MITM attacks pose significant threats, you can protect yourself by following these security practices:
- Use Secure, Encrypted Connections: Whenever possible, ensure that websites you use are secure and encrypted. Look for HTTPS in the URL, especially on websites where you input sensitive information. This layer of security encrypts the data, making it more challenging for attackers to decipher.
- Avoid Unsecured Public Wi-Fi: Public Wi-Fi is a popular vector for MITM attacks, as it’s often unsecured and widely accessible. Use a Virtual Private Network (VPN) when using public Wi-Fi, as it creates a secure, encrypted tunnel for your data.
- Enable Multi-Factor Authentication (MFA): Using MFA adds an additional layer of security, making it harder for attackers to access your accounts. Even if they intercept your password, they would still need the second authentication factor.
- Install Anti-Malware and Firewall: Robust anti-malware software can help detect and prevent MITM attacks. Firewalls also provide an extra layer of security by monitoring traffic and blocking suspicious connections.
- Keep Software Updated: Cyber threats evolve, and so do software security features. Regularly update your operating system, browser, and applications to minimize vulnerabilities.
- Be Cautious of Phishing Attempts: Many MITM attacks start with phishing emails. Be wary of suspicious emails and avoid clicking on links or downloading attachments from untrusted sources.
- Verify Website Authenticity: When entering sensitive data online, verify the website’s authenticity. Look for a secure padlock icon next to the website’s URL, indicating it’s encrypted.
Staying Vigilant in the Cyber World
MITM attacks are serious threats that can compromise personal and business data. Being aware of these attacks and following recommended security practices can help you protect your information and privacy. For more insights and tips on keeping your data secure, check out our resources on computese.com.
Additional Resources
For more details on cybersecurity threats and protection tips, consider visiting trusted resources such as Krebs on Security or Cybersecurity & Infrastructure Security Agency (CISA), where you can learn more about staying safe in the digital age.