This article explores the impacts of AI on software engineers and underscores why human expertise will remain crucial in this shifting landscape. The rapid integration of artificial intelligence (AI) into various technological domains is transforming software development at an unprecedented pace. With AI now capable of writing code, creating applications, and performing tasks that once […]
Ai is slowly forming society by what way? AI is slowly forming society, gradually weaving its influence across various facets of our lives, subtly forming a new societal landscape. From healthcare and education to daily conveniences and workplace changes, AI is transforming the way society functions. This shift isn’t always obvious, but AI’s effects are […]
Artificial intelligence (AI) is transforming homes with smart home devices that simplify daily tasks and create a more personalized, energy-efficient living environment. With smart thermostats, fridges, and lighting systems, AI-powered homes offer not only increased convenience but also energy savings by learning and adapting to users’ habits. Here’s how AI is making a difference in […]
Artificial Intelligence (AI) is reshaping health and wellness, bringing personalized care, early detection, and proactive health management to a new level. Let’s explore how AI-driven devices and apps are revolutionizing healthcare and what it means for our well-being. 1. Wearable Devices and Early Detection AI-powered wearable devices, like fitness trackers and smartwatches, are playing a […]
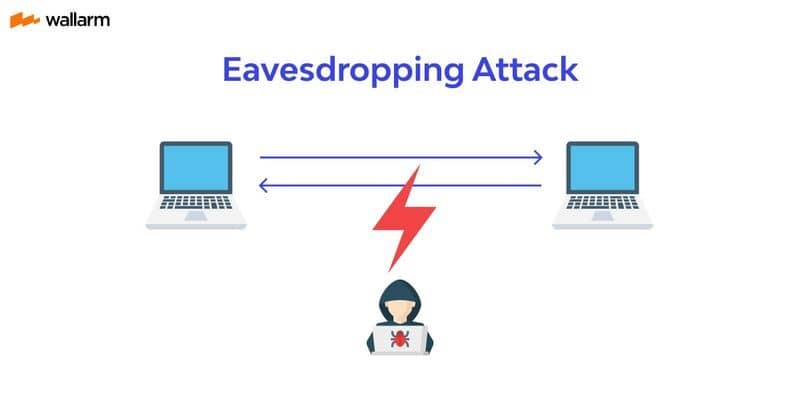
An eavesdropping attack is a form of cyber espionage where hackers intercept communications, typically over networks, to capture sensitive information. This type of attack is also known as network sniffing or wiretapping in digital spaces. Eavesdropping attacks can compromise personal privacy and expose critical business data, making them a significant security concern. In this article, […]
Snooping attacks are a form of cyber-espionage in which attackers secretly intercept, monitor, or steal data as it travels between devices or within a network. Unlike some overt cyber-attacks, snooping is often subtle, making it difficult to detect until after the damage has been done. In this article, we’ll explore the mechanics of snooping attacks, […]
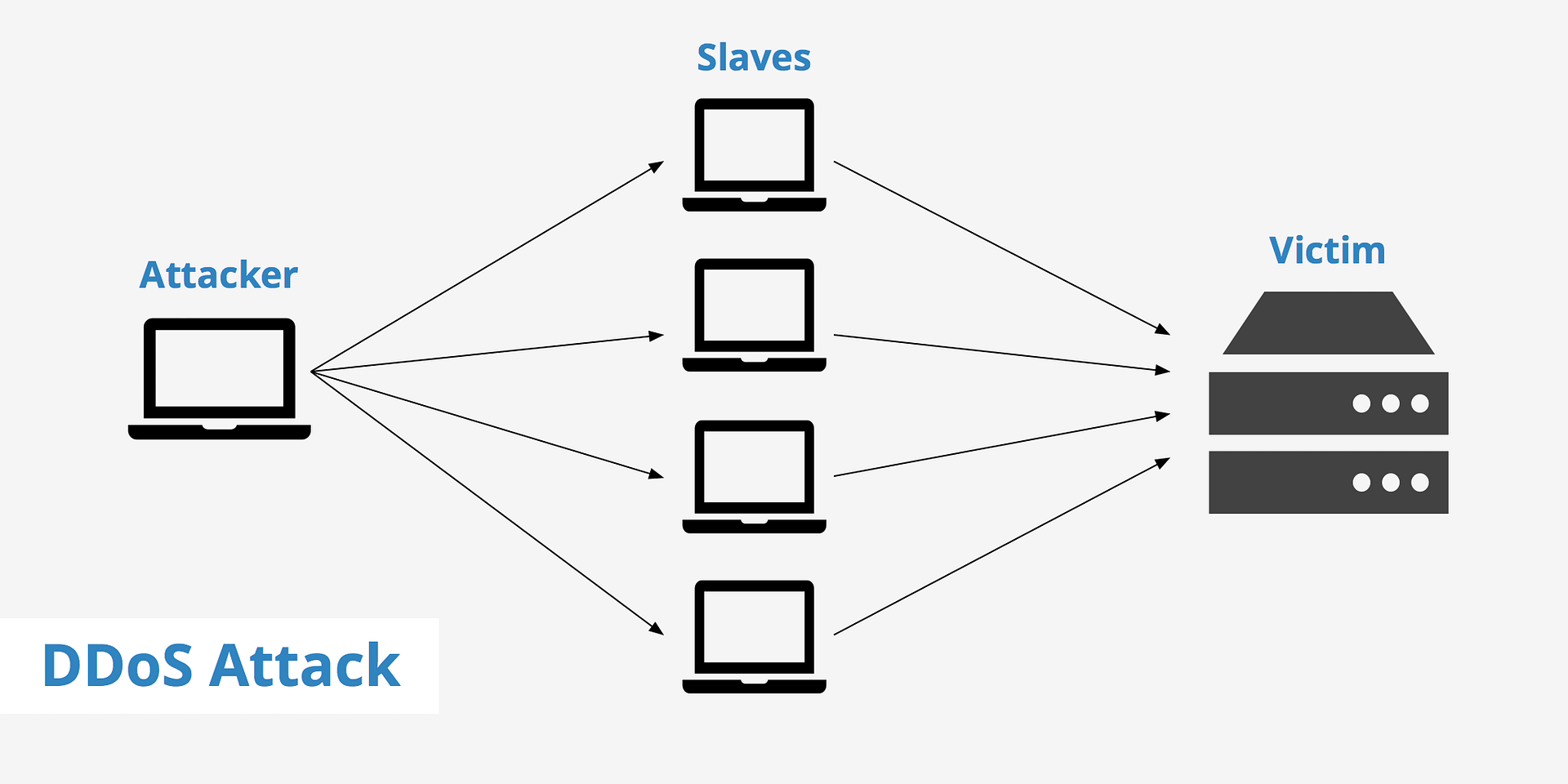
A Distributed Denial of Service (DDoS attack is a type of cyber attack in which multiple compromised systems flood a targeted server, service, or network, overwhelming it with traffic. This makes the targeted service unavailable to legitimate users. DDoS attacks are a significant threat to online businesses, government sites, and any organization reliant on internet […]
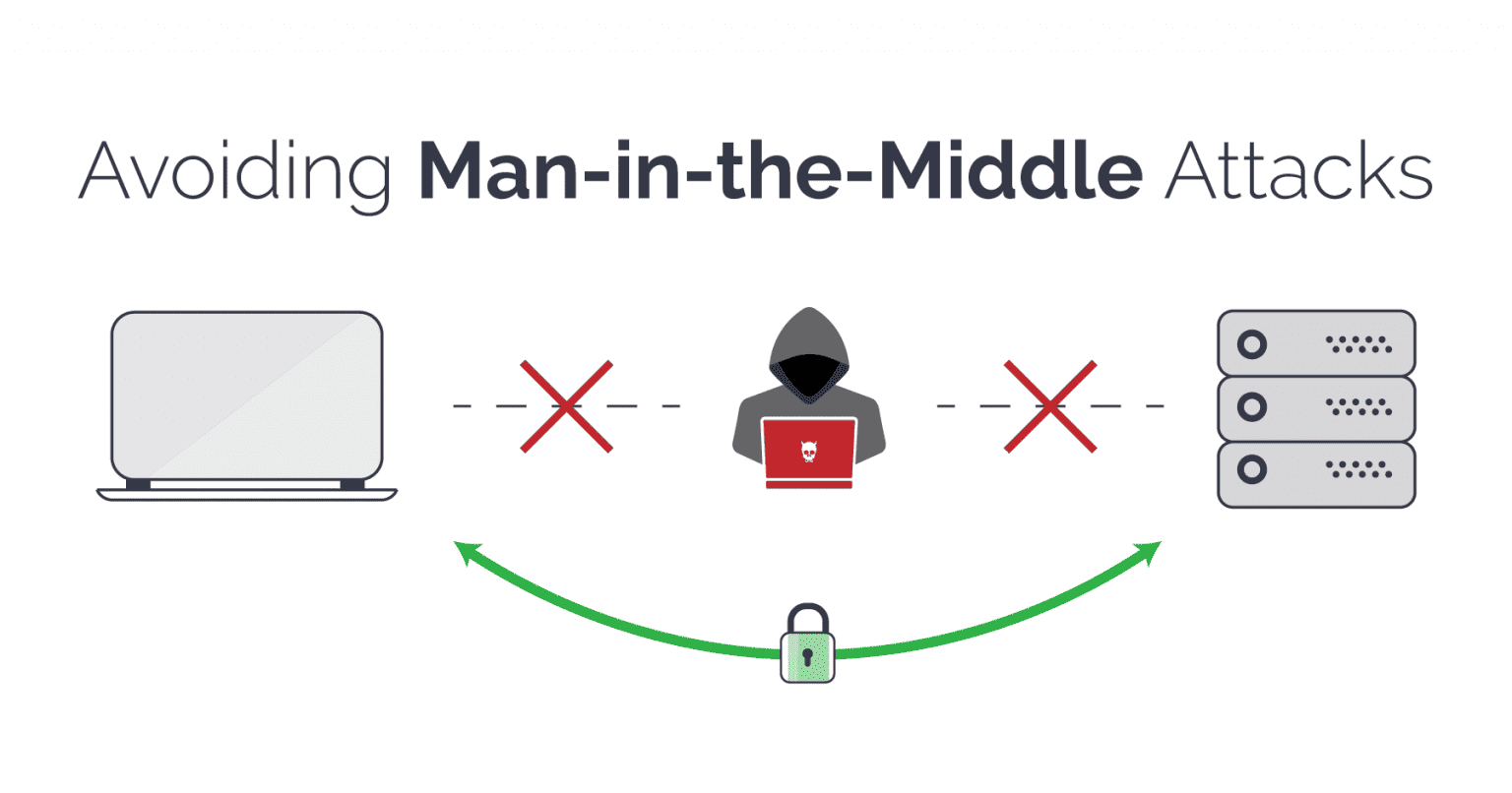
A Man-in-the-Middle (MITM) attack is a common yet severe cyber threat, where an attacker secretly intercepts communication between two parties, aiming to steal data, alter messages, or compromise security. This article will break down how MITM attacks work, provide real-life examples, and share essential tips to protect your data from these cyber threats. What is […]
On-page SEO plays a critical role in determining your website’s ranking on search engine results pages (SERPs). By optimizing the elements directly on your site, such as content, meta tags, and internal links, you can boost visibility and drive organic traffic. In this guide, we’ll dive into effective on-page SEO practices that will improve your […]
Improve Website accessibility is crucial in ensuring that all users, including those with disabilities, can access and interact with online content. By making websites accessible, not only do you meet legal requirements such as the Americans with Disabilities Act (ADA), but you also enhance the user experience and improve SEO performance. In this guide, we’ll […]